Generally speaking I get on very well with the KNX Home Automation standard and the ETS software used to configure a KNX installation, but every now and again it catches me out.
A recent situation was for the automated garage doors. Those are Hormann RollMatic 2 roller shutters and each one has a Hormann KNX Gateway attached to its HCP Bus. While these don’t provide a huge range of functionality, they do make it possible to open and close the roller shutters from the KNX Bus (e.g. using Home Assistant) and to trigger other actions when the shutters open and close.
The behaviour I wanted is that whenever one of the doors starts opening, it:
- Switches on the two Indoor garage lights either side of that specific door
- There are no windows in the garage and the garage doors are North-facing so it’s generally always desirable for the indoor lights to come on – though I’ll review that again in the Summer
- Switches on the two Outdoor garage lights either side of that door
- But only if it’s dark outside
- Switches on a relay to tell the alarm system that a door is being opened
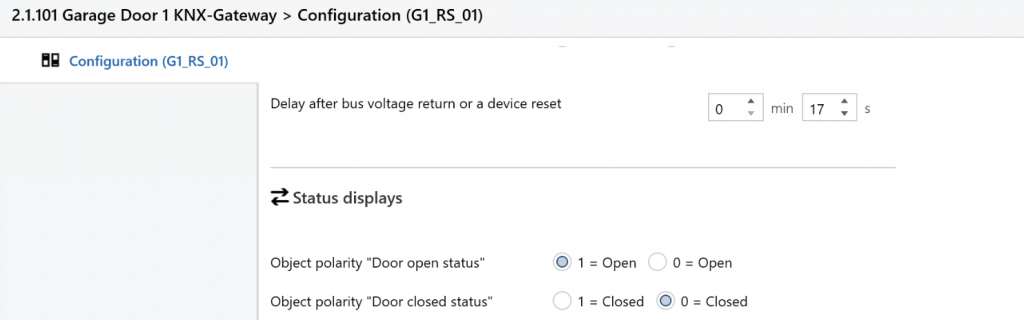
The Hormann KNX Gateway provides both a “Door open status” and a “Door closed status” output. At first glance “Door open status” looks like it will provide the necessary trigger but in fact that only changes state when the door is fully open – i.e. at the end of the motor travel. Fortunately there are configuration options to flip the “Object polarity” for both these outputs, and by selecting “Door closed status” to be “0 = Closed” (as shown below) that effectively becomes a ‘Not-Closed’ output, which changes to 1 as soon as the door starts opening.
The Hormann KNX Gateways were a relatively late addition to the installation, due to availability issues, so I’d previously configured separate KNX Group Addresses for each of the Lights to enable manual control using the Home Assistant app.
The mistake I made was to link the Hormann KNX Gateway’s “Door Not Closed” output to the multiple Group Addresses I’d already configured – and the problem is that only one Group Address can be configured as the “Sending” destination for an output object. Initial testing showed that my multiple-GA configuration sort-of worked – e.g. the indoor lights initially came on when a door opened – but once the other targets were configured the indoor lights stopped working.
The fix was to link all of the lighting relay channel switches directly to the same Group Address as the “Door Not Closed” output, so the latter is only “Sending” to that one GA. There are still dedicated Group Addresses for the lights, for use with Home Assistant, but those are no longer targets for the “Door Not Closed” output.
To complete the picture, the “But only if it’s dark outside” logic is addressed using a Group Address which tracks whether it is “Daylight” or not, and configuring that as a “Lock” for the relay channels connected to the Outdoor lights. When the Daylight GA is ‘On’ the Lock is active and the status change from the “Door Not Closed” output gets ignored for the Outdoor lights. The setting and resetting of the Daylight GA is performed using the existing Home Assistant Automation rules which run at Sunrise and Sunset (although using a KNX ‘Twilight’ sensor would be an alternative and more natively-KNX way of achieving that).
The only remaining minor issue is that some of the Indoor lights switch off when one of the garage doors gets to be fully closed – which is annoying when planning to continue working inside the garage with all the doors closed. That means using the light switch (or Home Assistant) to turn them all on again. In principle, it would be possible to use the motion sensors which are part of the alarm system to control (some of) the lights, but that integration isn’t currently in place.



